Smartphones are becoming deeply ingrained in society, advancing the technological communication that people use on an everyday basis. Software systems, such as the System and Method for Previewing Calls in Communications Systems, are being created and patented in hopes of improving smartphones and the efficiency they can bring to a user’s life. Based in the New Jersey Institute of Technology’s Department of Information Systems, Sukeshini A. Grandhi (then a PhD student), Professor Quentin Jones, and PhD student Richard Schuler III invented the System and Method for Previewing Calls in Communication Systems and patented it as US9226049B2 on December 29, 2015.
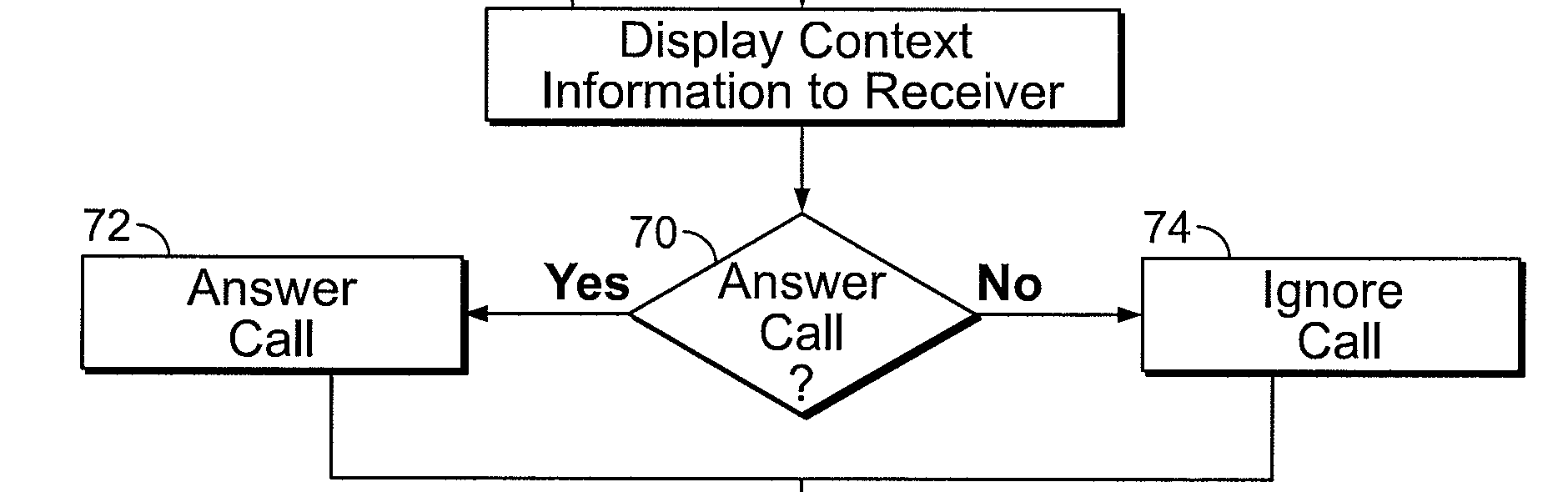
The patentees felt that the once-simple task of picking up a phone call had become time consuming because calls from scammers, automated marketing, and calls of low priority (perhaps those whom the receiver is trying to avoid or those whose calls aren’t urgent enough to pick up right away) may cause the receiver to answer a call they would rather ignore. The conventional phone call preview system consists of little information; when a caller (sender) makes a call to the callee (receiver), the callee’s phone interface provides them with either the name of the caller (if identity is known) or simply the phone number of the caller, the location in which the call is being made from, and options to either accept or decline the call. The NJIT researchers took this phone call preview system a bit further by providing both parties of a phone call with more information so that the receiver can make a more knowledgeable decision before they accept the call, while the initiator will know both when and why their phone call was either accepted or denied. This software system provides the additional information in the form of “fields” that the caller uses to identify themselves; they can also provide a short description of the subject of the call and a description of their current location. In addition to this, the caller can also provide a short description of an activity they are currently engaged in, the anticipated length of the call, the level of anticipated urgency, and emoticons that can be submitted in order to indicate the caller’s current mood. In a separate interface where the call log is featured on the caller’s phone, the caller can see which of their phone calls were answered or ignored by the receiver. The process of how all of these fields would be integrated into one system is clearly depicted in the Figure 3 from the patent.
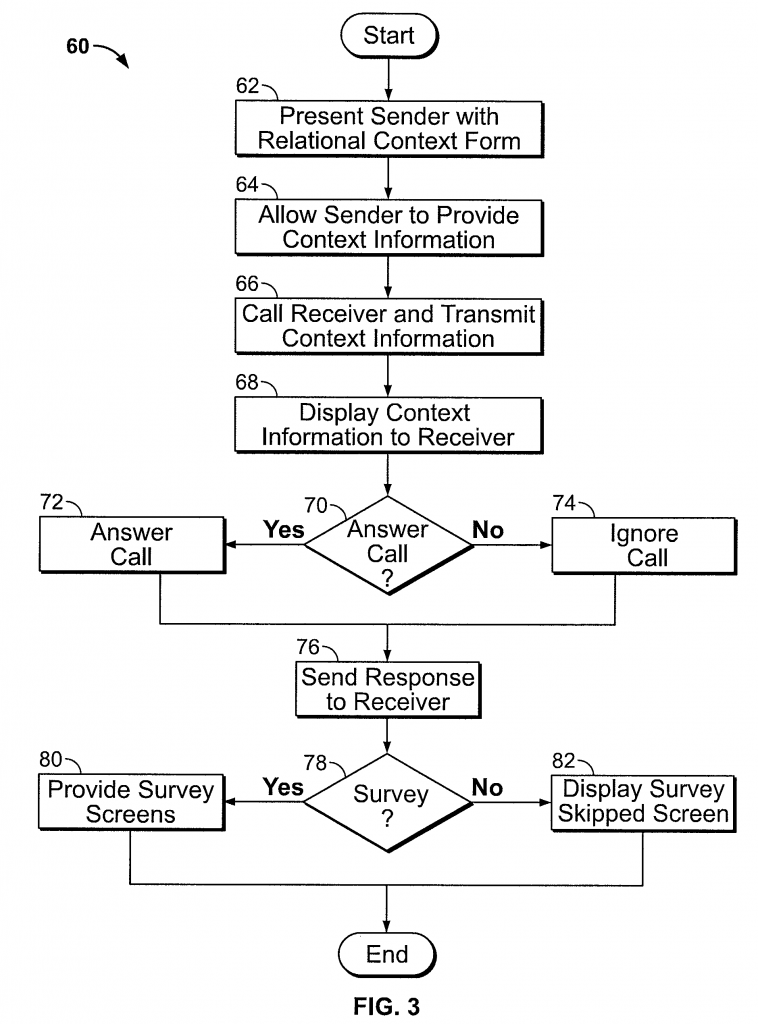
First, the call initiator would fill out a survey to provide the contextual information of the phone call. The recipient would then receive that provided information and have the option to answer or ignore the call. The recipient’s decision of what to do with the phone call will notify the initiator. The recipient can then fill out an optional survey at the end of the exchange to provide information on why they declined to answer.
There are thirteen other patents that the NJIT researchers cited, which display the range of activity in this field. These patents were also focused on enhancing the caller log system by either providing more information about incoming calls or managing the influx of incoming calls themselves. Some of the notable cited patents were those belonging to reputable corporate giants such as AT&T Corp. and Microsoft Corporation. Patent US6741689B2, which represented the work of AT&T Corp., was also a phone call system that aimed to supply a callee with information on the subject of the call. Patent US6977993B2, which was a product of Microsoft Corporation, also emphasized the importance of phone call context and opted to create an active notification system that provides call recipients with contextual information of a call (such as its subject and level of importance) via a phone notification invite. These other patents demonstrate an emphasis on better call preview systems—and a desire for techniques to save time—due to the numerous patents filed by prominent technology companies. In light of this competition it is important to note that while the technological ideas of incorporating more contextual information for phone calls and enhancing the organization of phone call notification systems were not new, the NJIT patent was the only one to incorporate all of the individual enhancements to the call preview system into one software system.
There were also eight patents that cited this specific system and method for previewing phone calls. Similar to the ones cited by the NJIT researchers, the later patents also covered common ground in terms of managing contact information and integration of systems involving call previews. Nokia Corporation, for instance, is one of the citers that mentioned and patented a system for information management. This management system provided phone owners with data regarding their interaction with their phone contacts; for example, it will keep track of and notify the number of times one has called and interacted with a specific number (US8856226B2).
What makes the NJIT patent particularly relevant is how call preview systems in general are so integrated within the technology of the modern day cell phone, and so the implementation of improvements to the original preview system could become commonplace and mainstream. The ubiquity of an improved call preview system goes hand-in-hand with its potential for practical benefits. The patentees created this telecommunications improvement so that people can potentially save time by picking up phone calls that are of immediate importance to them while knowing what calls can be ignored. Avoiding the phone calls that are not urgent or that are predicted to take longer than the allotted free time that person has for themselves will cumulatively contribute to that person’s time savings. The enhanced System and Method for Previewing Calls in Communications System would help people make conscious decisions of what conversations are worthy to pick up or delay for a better time.
By Victoria Nguyen